Tanya :
Saya sudah baca Tanya 213 : Memalsukan IP saat Mengakses SSH, Bisakah saya berselancar (menggunakan Firefox) dengan Tor agar IP address asli saya juga tersembunyikan ? Saya menggunakan Ubuntu Lucid
Jawab :
Bisa,
Berikut tahap-tahap dari awal untuk memasang, mengaktifkan serta menambahkan Tor di Firefox :
Instalasi Tor :
Keterangan : Tor adalah Onion Router generasi kedua. Dapat kita install dengan :
sudo apt-get install tor sudo apt-get install tor-geoipdb
Instalasi Polipo
Keterangan : Polipo adalah caching web proxy. Dapat kita install dengan perintah :
sudo apt-get install polipo
Konfigurasi Polipo
Pertama, untuk berjaga-jaga backup dulu file /etc/polipo/config
sudo cp /etc/polipo/config /etc/polipo/config.orig
Lalu edit file /etc/polipo/config – ganti dengan isi konfigurasi seperti berikut ini :
### Basic configuration ### ******************* # Uncomment one of these if you want to allow remote clients to # connect: # proxyAddress = "::0" # both IPv4 and IPv6 # proxyAddress = "0.0.0.0" # IPv4 only proxyAddress = "127.0.0.1" proxyPort = 8118 # If you do that, you'll want to restrict the set of hosts allowed to # connect: # allowedClients = "127.0.0.1, 134.157.168.57" # allowedClients = "127.0.0.1, 134.157.168.0/24" allowedClients = 127.0.0.1 allowedPorts = 1-65535 # Uncomment this if you want your Polipo to identify itself by # something else than the host name: proxyName = "localhost" # Uncomment this if there's only one user using this instance of Polipo: cacheIsShared = false # Uncomment this if you want to use a parent proxy: # parentProxy = "squid.example.org:3128" # Uncomment this if you want to use a parent SOCKS proxy: socksParentProxy = "localhost:9050" socksProxyType = socks5 ### Memory ### ****** # Uncomment this if you want Polipo to use a ridiculously small amount # of memory (a hundred C-64 worth or so): # chunkHighMark = 819200 # objectHighMark = 128 # Uncomment this if you've got plenty of memory: # chunkHighMark = 50331648 # objectHighMark = 16384 chunkHighMark = 67108864 ### On-disk data ### ************ # Uncomment this if you want to disable the on-disk cache: diskCacheRoot = "" # Uncomment this if you want to put the on-disk cache in a # non-standard location: # diskCacheRoot = "~/.polipo-cache/" # Uncomment this if you want to disable the local web server: localDocumentRoot = "" # Uncomment this if you want to enable the pages under /polipo/index? # and /polipo/servers?. This is a serious privacy leak if your proxy # is shared. # disableIndexing = false # disableServersList = false disableLocalInterface = true disableConfiguration = true ### Domain Name System ### ****************** # Uncomment this if you want to contact IPv4 hosts only (and make DNS # queries somewhat faster): # # dnsQueryIPv6 = no # Uncomment this if you want Polipo to prefer IPv4 to IPv6 for # double-stack hosts: # # dnsQueryIPv6 = reluctantly # Uncomment this to disable Polipo's DNS resolver and use the system's # default resolver instead. If you do that, Polipo will freeze during # every DNS query: dnsUseGethostbyname = yes ### HTTP ### **** # Uncomment this if you want to enable detection of proxy loops. # This will cause your hostname (or whatever you put into proxyName # above) to be included in every request: disableVia = true # Uncomment this if you want to slightly reduce the amount of # information that you leak about yourself: # censoredHeaders = from, accept-language # censorReferer = maybe censoredHeaders = from,accept-language,x-pad,link censorReferer = maybe # Uncomment this if you're paranoid. This will break a lot of sites, # though: # censoredHeaders = set-cookie, cookie, cookie2, from, accept-language # censorReferer = true # Uncomment this if you want to use Poor Man's Multiplexing; increase # the sizes if you're on a fast line. They should each amount to a few # seconds' worth of transfer; if pmmSize is small, you'll want # pmmFirstSize to be larger. # Note that PMM is somewhat unreliable. # pmmFirstSize = 16384 # pmmSize = 8192 # Uncomment this if your user-agent does something reasonable with # Warning headers (most don't): # relaxTransparency = maybe # Uncomment this if you never want to revalidate instances for which # data is available (this is not a good idea): # relaxTransparency = yes # Uncomment this if you have no network: # proxyOffline = yes # Uncomment this if you want to avoid revalidating instances with a # Vary header (this is not a good idea): # mindlesslyCacheVary = true # Suggestions from Incognito configuration maxConnectionAge = 5m maxConnectionRequests = 120 serverMaxSlots = 8 serverSlots = 2 tunnelAllowedPorts = 1-65535
Simpan kembali file /etc/polipo/config tersebut.
Menjalankan Tor dan Polipo
Jalankan Tor dan Polipo dengan perintah
sudo /etc/init.d/tor start sudo /etc/init.d/polipo start
Cek apakah sudah berjalan
Mari kita cek apakah Tor dan Polipo sudah berjalan di port 9050, lakukan dengan perintah
ss -aln | grep 9050
Jika anda mendapati keluaran seperti contoh :
0 128 127.0.0.1:9050 *:*
Maka berarti Tor dan Polipo sudah berjalan.
Menambahkan Add-On Tor Button di Firefox
Selanjutnya kita akan menambahkan add-on Tor Button di Firefox.
Download add-on tersebut di : https://www.torproject.org/dist/torbutton/torbutton-current.xpi
Install dan restart firefox anda, maka di sudut kanan bawah anda akan mendapatkan Tulisan seperti tampak pada screenshot berikut :
Untuk mengaktifkan, cukup klik tulisan itu. Lalu pilih Toogle for Status
Tanda bahwa Tor Anda telah aktif, tulisan berubah menjadi Hijau :
Kini coba test apakah Tor sudah aktif dengan mengunjungi situs uji : https://check.torproject.org/
Jika sudah aktif, maka halaman yang muncul adalah seperti berikut :
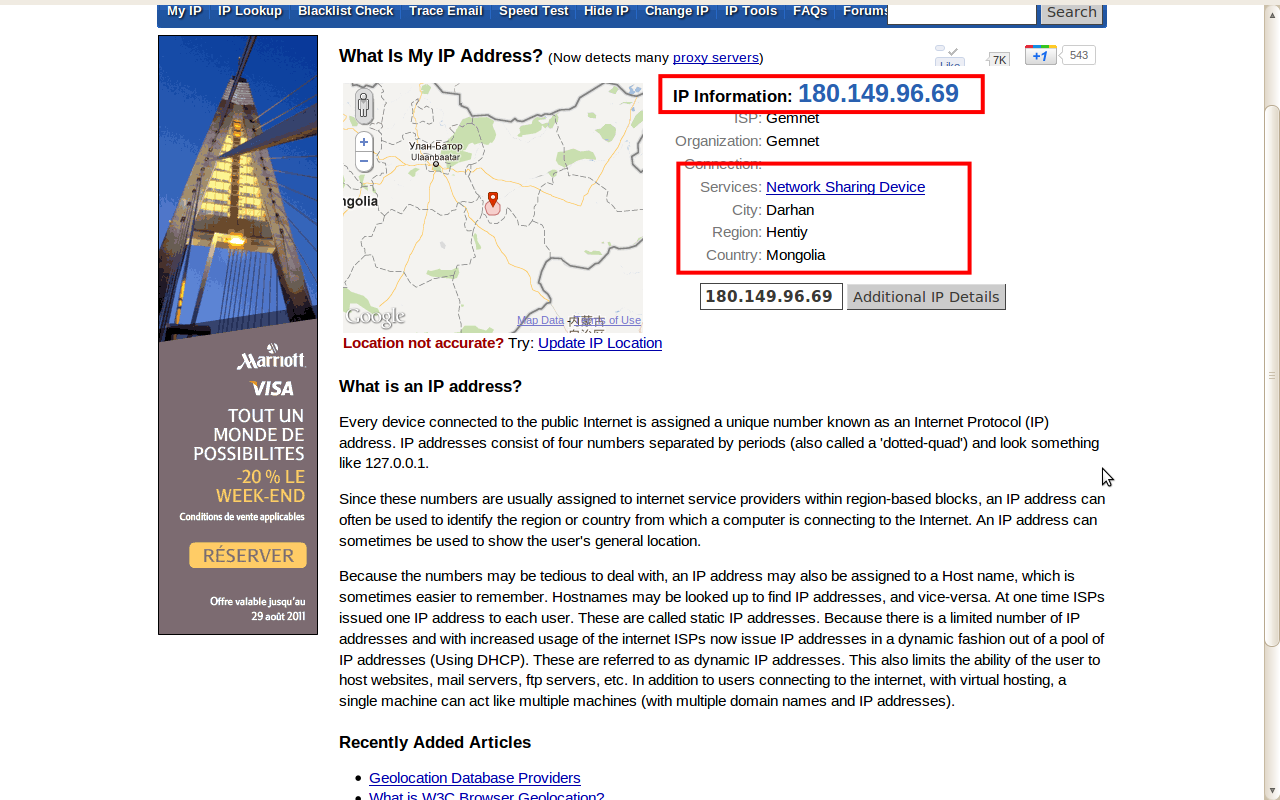
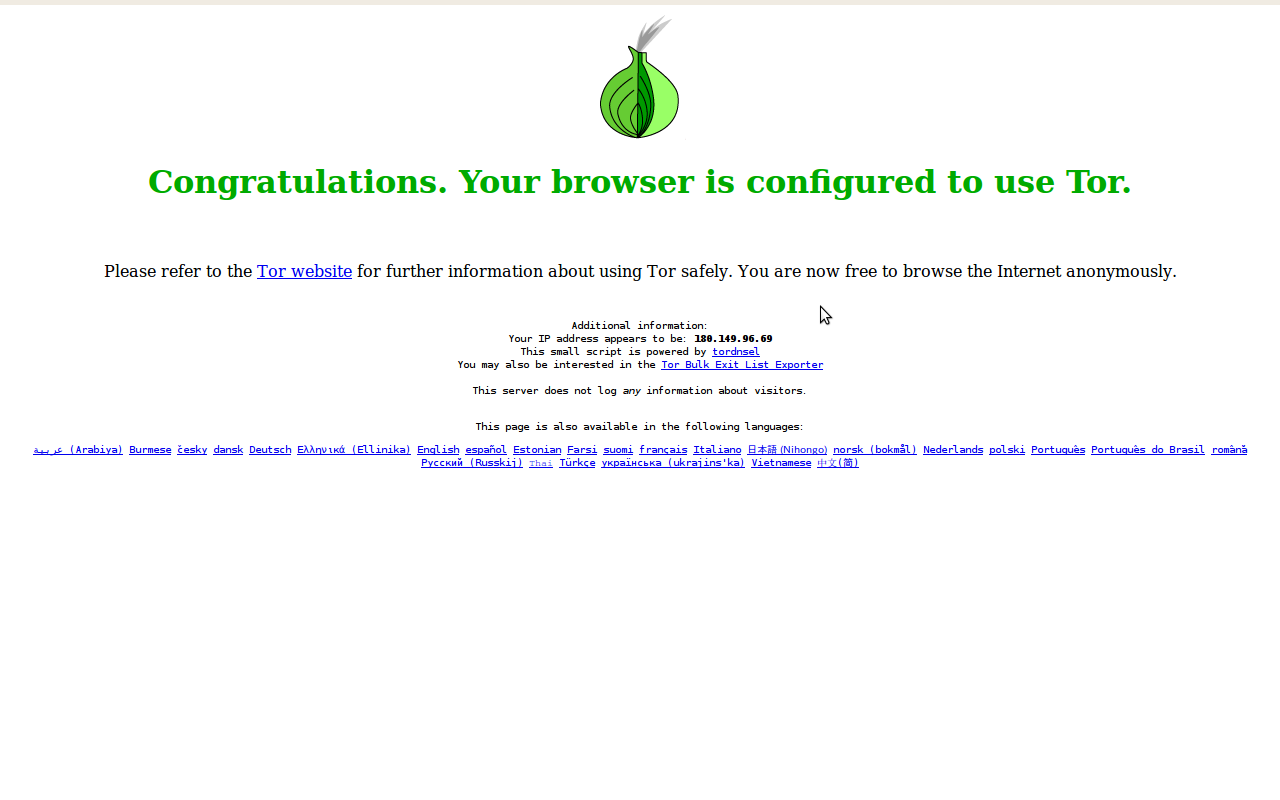 Lalu kita lihat berapa IP yang kita gunakan dengan mengunjungi situs http://whatismyipaddress.com
Lalu kita lihat berapa IP yang kita gunakan dengan mengunjungi situs http://whatismyipaddress.com
Vidalia : GUI untuk Tor (Opsional)
Anda juga dapat mengistall GUI untuk Tor, misalnya Vidalia, Install dengan perintah :
sudo apt-get install vidalia
Demikian selamat mencoba. Semoga bermanfaat (rezaervani@gmail.com)
Artikel Terkait
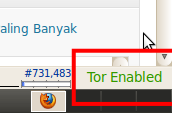
Kalo misalnya user mengakses website saya dan saya ingin melacak IP-nya menggunakan PHP, sedangkan pengguna menggunakan Tor. Adakah cara untuk mendeteksi bahwa IP yang digunakan adalah palsu? Lalu adakah cara untuk mengetahui IP yang sebenarnya saat pengguna mengakses website?
Untuk melacak IP Tor dengan php cukup mudah, tapi menemukan IP asli yang menggunakan layanan Tor tidaklah mudah. Bahkan di situs Torproject mereka mengatakan hampir mustahil men”trace” IP asli pengguna Layanan Tor.
Beberapa situs besar seperti Wikipedia bahkan sudah melarang pengguna IP Tor untuk mengedit suatu artikel di Wikipedia, walaupun tetap bisa membaca.
apakah ini juga berlaku ketika kita menggunakan koneksi dial up pada ubuntu 11.10?